

How Identity Theft Happens And How To Protect Yourself Against It
All about how identity theft happened and how we protect against them.
Technology has made it possible to give us an easy social recognition. Also, it is only due to this trending technology that we have now become more expressive. Our voice, ideas, feedbacks, comments can now easily yet effectively reach to masses, irrespective of the region. We can now share our happiness, our emotions, creativity not only with our family but also to the strangers. All in all, technology has played a vital role in bridging distance and eliminating territorial boundaries.
But since everything has one good and one bad aspect, same goes with technology as well. On one side where it has helped one to strengthen his identity, on another side it has also opened the doors for identity theft. Unfortunate but true!
What is Identity Theft?
Identity theft a word quite prevailing these days refers to an illegal gathering of the private information to impersonate as a genuine user and making the fraudulent activities. Identity theft can be made possible in a number of ways but the most common out of them are via infected links, phishing emails, pirated software.
How does Identity Theft Happens?
Although most of us are living in this digital world and using Computer from decades still very few of us are aware that most of our personal information is saved at a different location on our system. Your personal emails, the browsers, the system registries, personal documents are some of the areas where your personal and sensitive information remains stored. And what more it can be quite easily accessed by hackers to access and misuse this private information.
Now once the hacker gets hold of your personal information they can use it in numerous ways like online purchasing, creating fake accounts on social sites and others impersonation as you. And this will not hurt you monetarily but also emotionally.
How to Protect Yourself from Identity Theft
Now, since we already know how identity theft happens, it’s now time to learn about how to protect our self against it. Since most of our novice users therefore manual protection against identity theft can be a tough task. Also, most of us are completely unaware of the Windows registry, a place that stores of confidential information, therefore manually managing our identity traces is not everyone’s cup of tea. Therefore, to effectively protect all such sensitive information from identity theft we will need a third-party tool.
In this article, we are going to discuss one such tool named as Advanced Identity Protector that will give you complete protection against identity theft.
Advanced Identity Protector: Tool for Complete Protection against Identity Theft
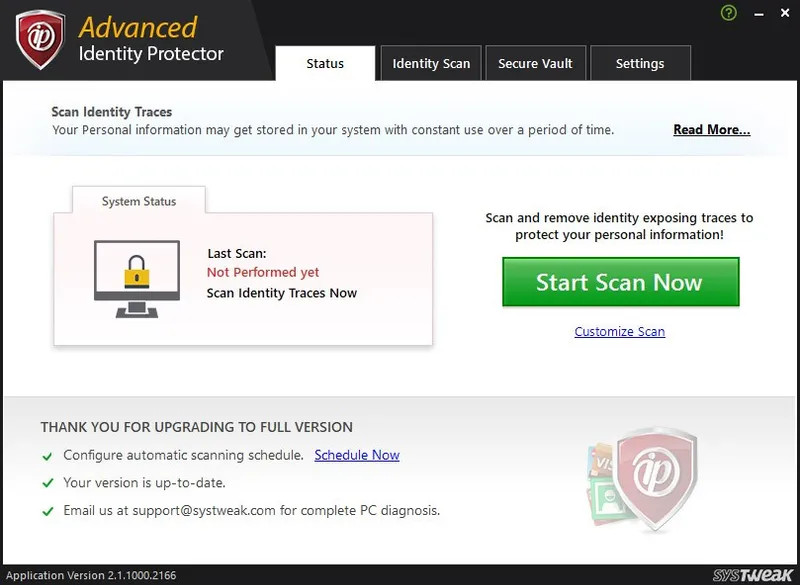
Advanced Identity Protector, a tool developed by Systweak is the best identity protection tool that guarantees personal information like your passwords, credit card information, email accounts, social security number etc. can only be accessed by you.
How to Use Advanced Identity Protector?
Advanced Identity Protector is the simplest tool for identity protection. After downloading and installing this amazing identity theft protection tool all you need to start a scan by clicking on Start Scan button.
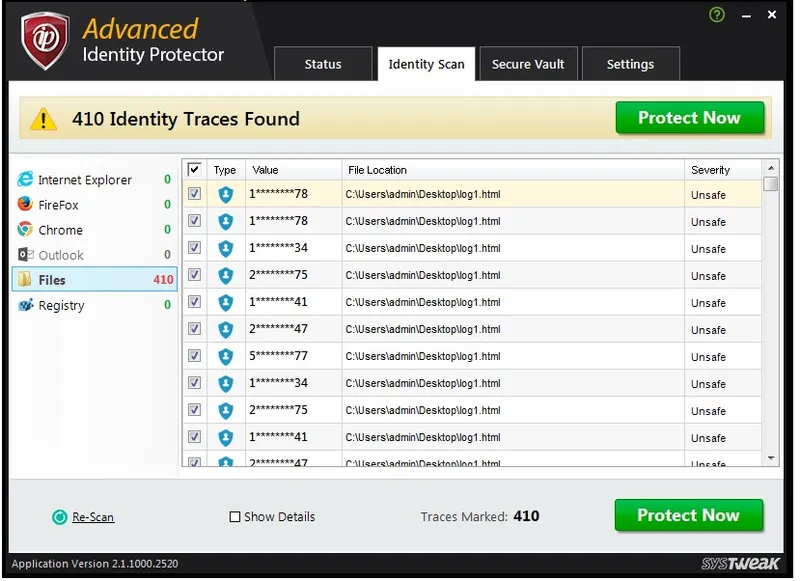
Now the product will deep scan your entire system for all the identity traces that can expose your privacy. When you have a close look at these hidden traces, you will find that these traces consist of the most private information like credit card and social security numbers, email id and passwords etc. Shocked, but yes, all these traces are on your system. And all these can be easily accessed by a hacker by simply taking remote control of your PC or planting malware on to your system.
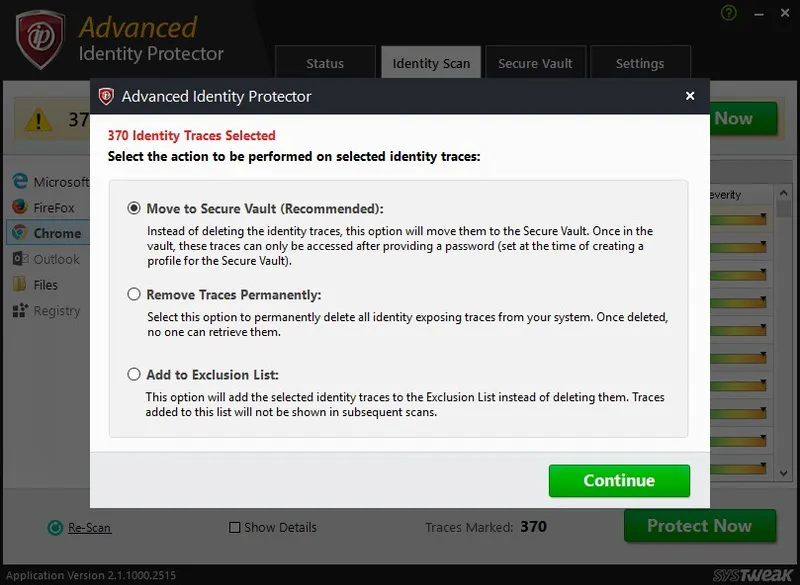
Now once all the privacy traces are detected by Advanced Identity Protector, you have two choices to deal with them. First, you can delete all these traces completely from your system. And, second, you can save then in the Secure Vault of the product.
If you choose the second option and move all the traces to Secure Vault, then the information is completely encrypted and can only be decrypted by a password that is known by you.
In this way, this amazing tool will protect all your confidential traces from the prying eyes and keep your personal details intact.
Author :- Chandra Shekhar Choudhary is working as an SEO analyst and technical Content Writer. His potential of writing is PC tips, Android and Mac tricks, identity theft protection and he is anxious in writing other technical blogs. You can also find Chandra Shekhar on Facebook, Twitter and Instagram.




