98% of e-commerce apps you use are vulnerable, finds report

Next time you install an e-commerce, taxi booking or food delivery app, take a look at all the details you will be sharing—everything from contacts and location to photos and SMS details. A study by automated mobile app security scanner, Appvigil, has found that 98% of the top 50 e-commerce mobile apps are vulnerable to security attacks.
The study comes at a time when more and more new-age Internet commerce companies are becoming app-only or are becoming increasingly reliant on mobile apps for transactions. Flipkart’s fashion e-commerce subsidiary Myntra went app-only earlier this year. Snapdeal launched Shopo, as an app-only platform in July. Most of the new hyperlocal startups like Swiggy or Grofers are also predominantly app-only.
Consumers too have taken to mobile for their online transactions. Over 75% of Snapdeal’s sales are through mobile channels. Competitor Flipkart too has similar mobile transaction numbers.
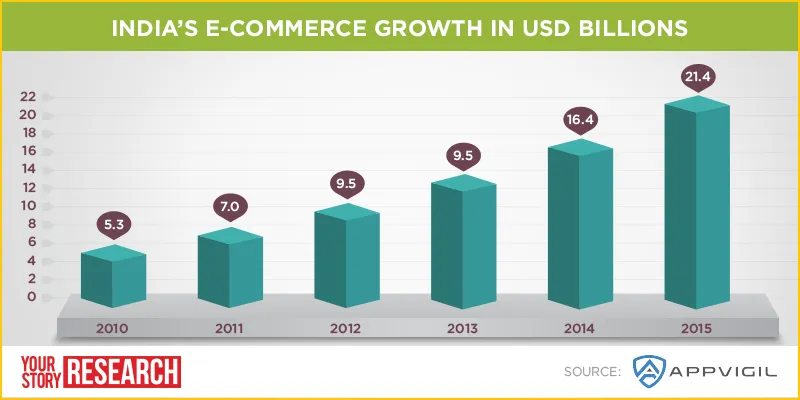
A study by advisory firm Deloitte estimated that revenues from paid apps in 2015 would cross Rs 1,500 crore.
These numbers and data show just how important apps have become and how important app security is. Already, reports have emerged on many top Indian startup apps getting hacked. Ola, ZopNow, Zomato, Foodpanda, and Gaana apps reportedly had security issues and were hacked. Many of these companies have, however, denied that security breaches have occurred.
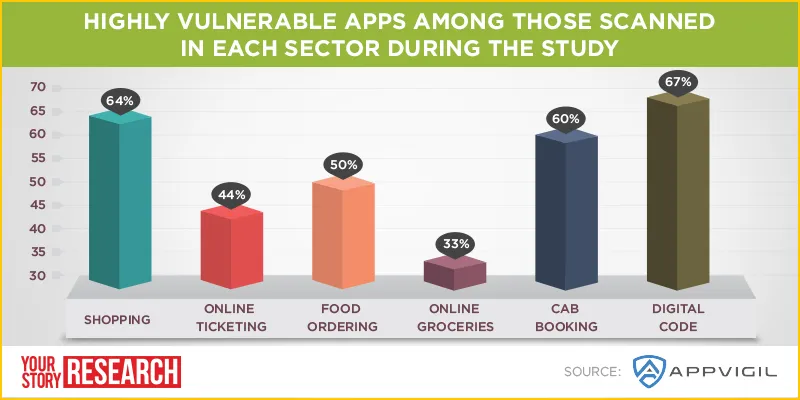
Appvigil’s study, ‘Security Report of Top 50 e-commerce Mobile Apps’, has found that nearly 80% of the 50 apps studied were vulnerable to hacking.
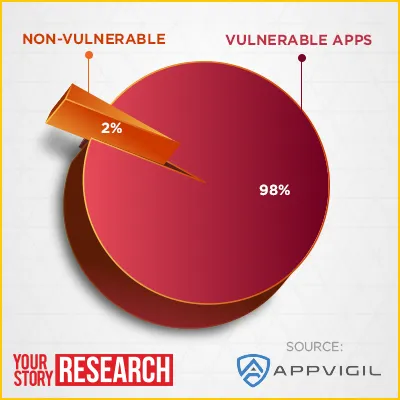
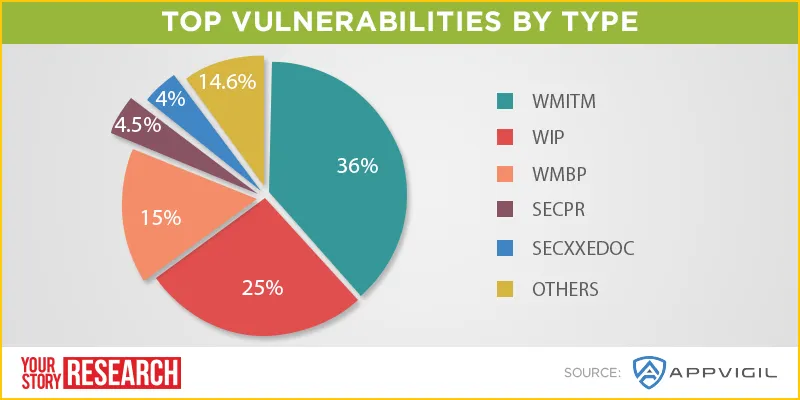
Appvigil found that a significant number of apps have more than 50 vulnerabilities. High and medium level severity vulnerabilities comprise more than 90% of the total 1,243 security vulnerabilities found from the 50 scanned apps. Curiously, no app was found that had only low level severity vulnerabilities.
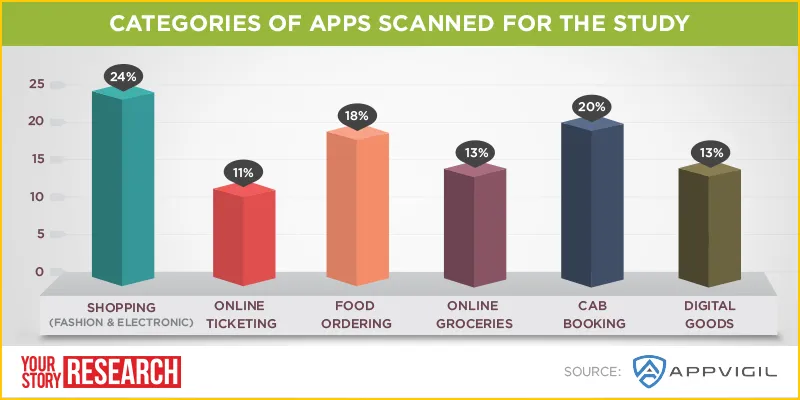
For Appvigil’s study, the default criterion was to cover all apps which facilitate financial transactions through them and the mobile apps that are top ranked in the Google Play Store under different categories were chosen.
“We performed the security analysis on Appvigil, which requires only the executable APK file of an Android app,” says Toshendra Sharma, Founder and CEO, Wegilant - Appvigil. All the apps went through stringent analysis on Appvigil: the byte code structure of the app was studied to look for any vulnerable connection and patterns, the run time behaviour of the apps was tested against the vulnerabilities in an emulated hacking environment, and all the network calls (API) were monitored.
Impact on the industry
“The fact that the customer’s information is leaked implies that the app did not take security seriously which shows it is not very loyal to its customers. Customers usually do not get back to the apps (unless the apps doesn’t have any competition) that are known to be compromised,” says Toshendra. In some scenarios all the related apps gets effected – Ashley Madison hack giving a sudden jolt to its counterpartsbeing one such instance.
The study found that even basic security practices have not been setup, threatening the privacy of millions of users. “This will surely deter more users from adopting the online platform affecting the reputation of the companies in the longer run,” the report says.
Besides e-commerce sites, dating and fitness apps are also prone to hacking. “Imagine if information on a dating app user’s interactions, interests and other details are leaked due to insecure authentication implementation, well, you can guess the consequences,” says Toshendra Sharma.
How to secure yourself?
“The average developer is not cyber security savvy. But developers must constantly update themselves with industry’s best practices,”says Ravi Gururaj, serial entrepreneur, angel investor and startup mentor.
An app can be a malware which attacks other apps or mobiles to extract critical info. An app used by a consumer could be vulnerable and prone to attack by the malware app.
To tackle the first one, the user should make sure the downloaded app is not a malware by using a mobile antivirus solution. Addressing the second one is more critical as zero day malware, which is malware only the creator knows and the developer doesn’t, cannot be stopped by antivirus (until the signature of the malware is updated), says the report.
After an app is downloaded, services like that provided by Appvigil can let the user know if it is vulnerable.
Experts say the primary responsibility lies with developers to protect consumer data, especially when users are quite permissive with access to information in the app environment.“Unfortunately, startups hire only marketing officers first, and security officers last. It should be the other way round,” says Ravi.







